15/2/2023
A Brief Introduction to Nostr
“A milestone for open protocols…” This is how Jack Dorsey, co-founder and former CEO of Twitter, announced the arrival of the Damus app, a Nostr protocol client, in the App Store/iOS.
Nostr has generated buzz in developer groups, bitcoin addicts, and a crowd very suspicious of their own shadows. The reason: Nostr brings an alternative to commercial social media that, in the words of its creators, would be “truly censorship-resistant.”
But Nostr isn’t a new social network. Nostr is a protocol, something more like the web (HTTP/S) and email (IMAP/SMTP) than Twitter or Instagram.
In practice, Nostr is a foundation on which developers build applications. Its main differentiator is the authentication system, based on cryptographic keys. Experts praise the simplicity of the protocol, which in theory facilitates the development of apps.
(Hold my hand and come with me because now things get a little weirder).
To create a profile/an identity in Nostr, you need to enter or create a pair of keys:
- One of these is private and functions as the “password” for logging into the apps. It is vital to guard the password well, because if you lose it, there is no way to regain access to the account, and if someone finds out, they can impersonate you and there is no way to reverse it.
- The other is the public one, and it is the equivalent of your @username on Nostr. When you share your profile you do not indicate an @username, but your public key.
Both keys are jumbles of letters and numbers. It is like that code from Nintendo’s virtual network, only (much) worse.
Want to follow me on Nostr? Search for npub1wa406lmdvfctavg3qgwauwrg228ylvskcyj0prfh48e0xwv6aensyv5n87.
Yeah, I know.
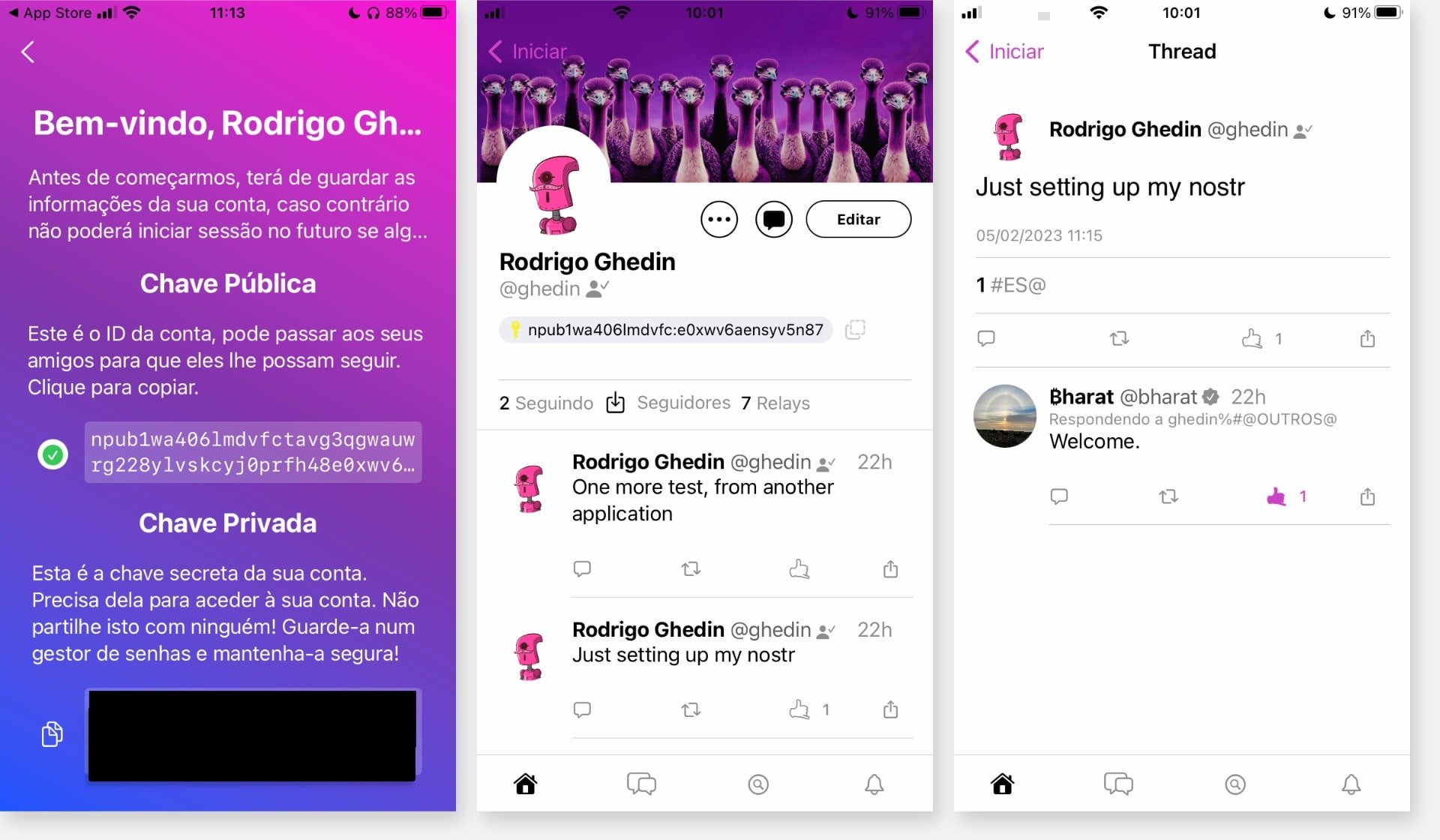
With your private key, you can log into any app and feel at home with your content and connections.
Another difference of Nostr to conventional social networks is that the structure is based on “relays,” as if they were “nodes” in a peer-to-peer network.
“[Relays] allow Nostr clients to send them messages, and they may (or may not) store those messages and broadcast those messages to all other connected clients,” says Nostr.how, a good interactive Nostr tutorial.
In Nostr.watch you can see the active relays in real time and details such as latency and country of origin. At the time of writing this there are 282 active relays worldwide.
I created my profile in the Damus app and then logged into Iris, a web application (see my profile). And… it works!
When I logged into Iris, I could see the system communicating with the relays — my posts didn’t appear immediately. In one corner of the screen of both apps, Iris and Damus, you can see the number of connected relays.
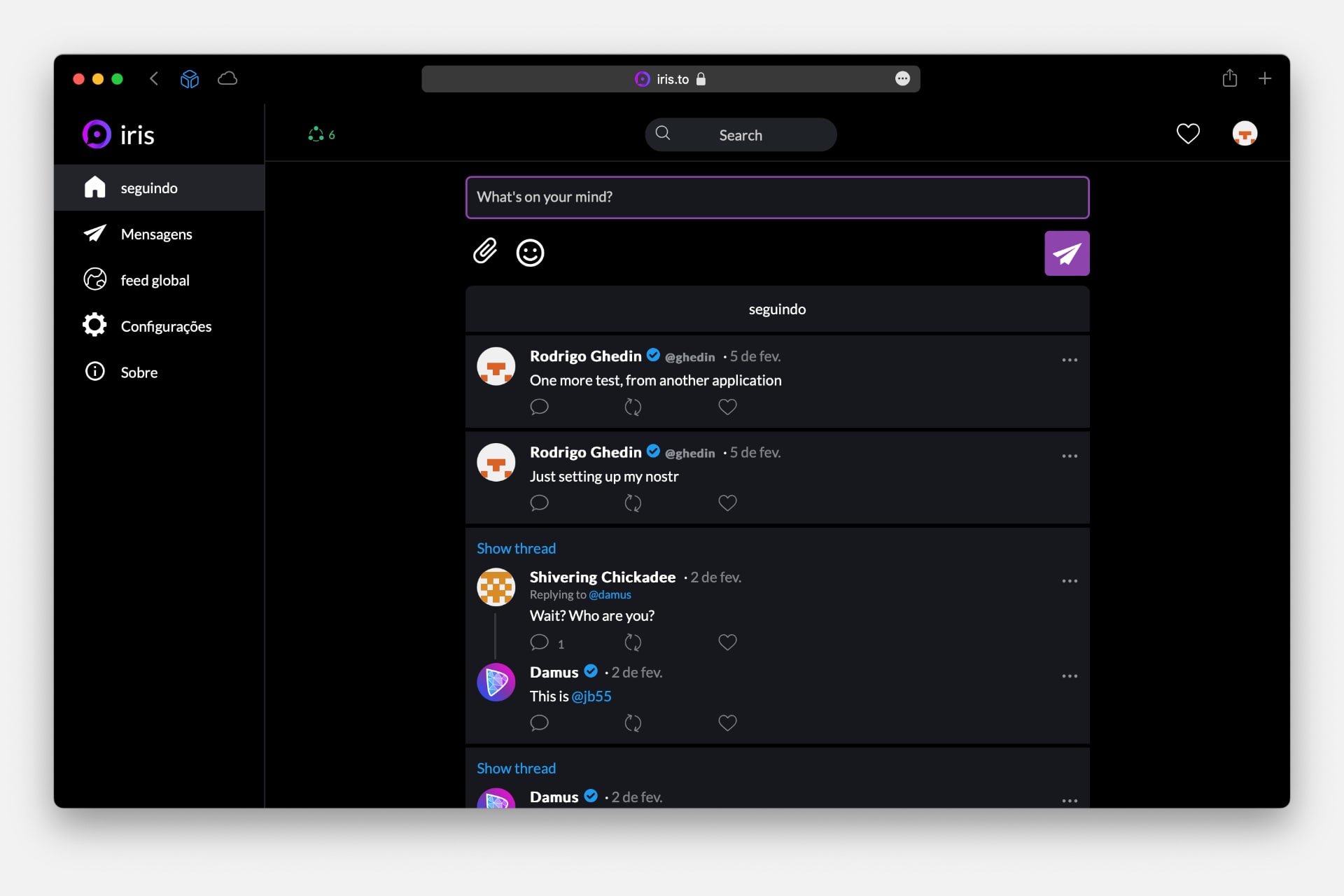
Both apps are very reminiscent of Twitter, with a timeline, posting box, and direct messages, which here are encrypted end-to-end.
It doesn’t have to be this way, however. Being a protocol, Nostr allows the creation of very different apps on top of it.
On this site and in this list are different apps based on the protocol, such as Jester, a chess game, and Alby, a bitcoin wallet.
Nostr is a kind of “end-of-the-world protocol,” designed for extreme situations where absolute mistrust reigns between those involved — users, relays, and app providers.
If in Twitter you have to trust Twitter, and in Mastodon, the administrator of your instance/server, none of this is necessary in Nostr. The protocol is truly decentralized and its using, although connected, is independent of other parties.
Even the identity verification system, called NIP-05, is independent of external validations. It is done based on DNS records.
To the creators and promoters of Nostr, the great appeal is an almost full resistance to “censorship”. We know where this conversation is taking us, and… it’s not a good place.
Despite the support of influential people in the industry, like Jack Dorsey, Nostr sounds at the moment like something too complex for mass adoption — far more complex than Mastodon, for example — and without much appeal to normal people who just want to have a laugh on Twitter and look at pictures of celebrities, food, and friends on Instagram.
Much of the complexity lies in the pair of keys thing. Which is not new; This is a recurrent thing among those who work with servers and development. Although they have many advantages, it’s risky and difficult to understand for those who are not in the business.
It is no wonder that commercial apps often use abstractions, such as login and password, to make it easier for more people to use them. If people can’t keep passwords, imagine a kilometer-long pair of cryptographic keys?
My bet? It might work, but it will be niche, like other creative little protocols that pop up from time to time, such as Gemini, an alternative to the web that looks like the web of the 1990s.